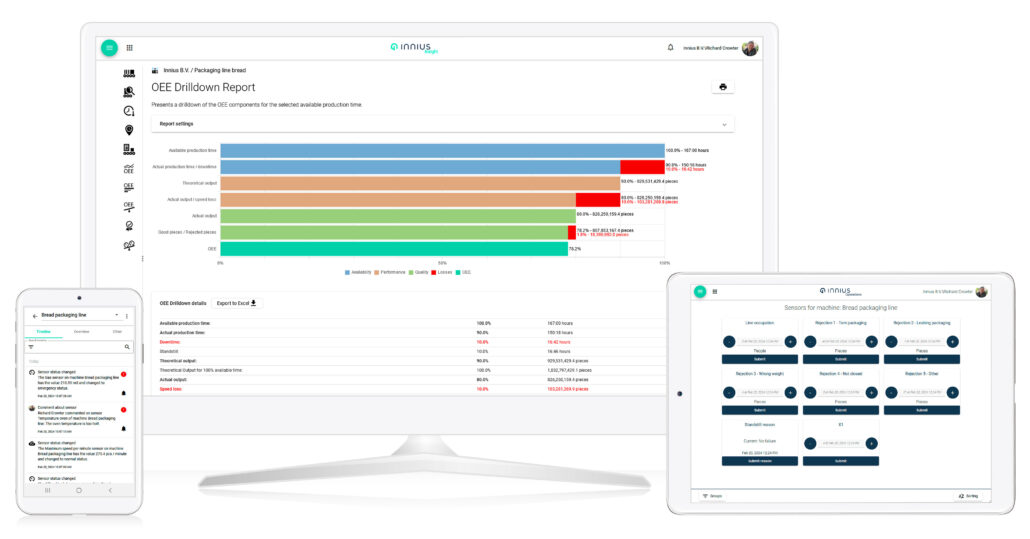
The innius Industrial IoT platform
The innius® platform caters to the needs of plant managers, maintenance teams, and production line operators, offering a comprehensive suite of tools and applications. Alongside the Connectors and Integrations, including those for dashboards, the platform features three primary Apps: the Admin app, the Insight app, and the Operations app. The Admin app is a web-based app that facilitates configuration and data enrichment. The Insight app delivers accessible data analytics with both web and mobile-based apps for Android and iOS devices. The Operations app allows manual data collection by production line operators via a web-based interface optimized for touchscreen laptops and tablets.